**NOTE: The app being analyzed is not my own, and therefore I have left out any identifying information. This is just a walkthrough of the steps one can take to search for similar vulnerabilities.
This walkthrough will show how to use cycript to extract information from the app at runtime, allowing the attacker to access the app’s PIN.
This bug was discovered using a jailbroken iPhone 5s running iOS 10.2. Note that earlier/later versions of iOS may not be compatible with the tools used here.
1) Clutch
We will be using ‘Clutch 2’ (a public iOS decryption tool) to decrypt and extract the app’s .ipa file, which we will later need to dump and examine the Objective-C headers of the app’s classes.
Clutch can be downloaded here : https://github.com/KJCracks/Clutch
Follow the installation instructions to get Clutch on your device.
If you run Clutch2 and see a 'Permission Denied' error, you may need to run this command first:
$ chmod a+x /usr/bin/Clutch2You can then run:
$ Clutch2 -iAnd you will see a list of your installed apps. Pick the app you intend to work with and copy it’s bundleID value.
Next run:
$ Clutch2 –b <BundleID>You should see a message telling you that the cracked binary was dumped with a path to where it was saved.
Next, you will want to transfer the binary onto you Mac for analysis. You can do this in many ways, but I prefer to use CyberDuck. You may use any suitable file transfer software, or you could just ssh in to your phone and scp the .ipa to your computer.
Once you have the .ipa on your laptop, you can simply unzip the file to gain access to its contents. (You may have to manually change the file type to .zip before doing this).
2) class-dump
The next step will be to dump the app’s runtime headers using a tool called class-dump. You can install this on your computer with brew by running:
$ brew install class-dumpFirst, find the app’s executable. You will find this in the .ipa folder you copied to your computer, at the path /Payload/<AppName>.app/AppName.
Run:
$ class-dump /Payload/<AppName>.app/AppName > dumpedHeaderswhere ‘dumpedHeaders’ is the file you are creating where the dump will be written to.
Now you should be able to view ‘dumpedHeaders‘ in any text editor like Sublime. For this app, we open up the file and search for anything that might be interesting. I start by searching for terms like ‘authorize’, ‘login’, or ‘pin’. I quickly come across what I’m looking for:
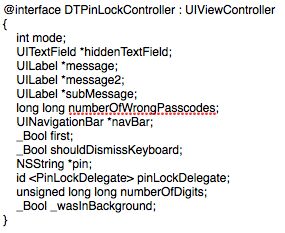
I can see that inside the DTPinLockController class, there is property NSString *pin. Now that I have found a target, I can move onto the next step.
3) cycript
First, download cycript onto your computer by downloading the latest version here: http://www.cycript.org/
Then, put cycript on your device by transferring the file over (via CyberDuck, sftp, scp, or whatever you prefer).
Finally, while ssh’d into your phone install by running:
$ dpkg -i cycript.debNow you can try running cycript and confirm that the #cy prompt appears. (Make sure to exit cycript before the next step).
Now we are ready to hook into our target app’s process. To find the app’s process ID, make sure the app is running on your phone and run:
$ ps auxCopy your target app’s PID, and then run:
$ cycript -p <PID>You are now hooked into the process and can begin exploring the app at runtime.
Since this app requires a PIN to enter, at this point my app is open on my phone and is at the ‘Enter PIN’ screen.
To confirm the the name of the ViewController I am seeing, I run in cycript:
cy# UIApp.keyWindow.rootViewControllerAnd get back:
DTPinLockControllerNow, looking back into my class-dump, I can see that this is indeed the screen that I found the ‘pin’ NSString property on earlier, and thus I should be able to access its value at runtime. To see if the PIN is stored insecurely, I run:
cy# UIApp.keyWindow.rootViewController.pinAnd magically, the user’s PIN is spat right out:
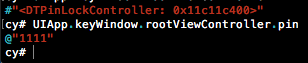
Now we have successfully stolen the user’s PIN during runtime. I can confirm this by simply entering the PIN on the app, and I am granted access.